Minimum data fields 2 – Digital Certificates and Certification Authorities
- Certificate Authority Key ID (Not Critical): An identifier of the CA’s public key in case it has several public keys in use. It is recommended to use the hash value of the public key as an identifier.
- Certificate Subject Key ID (Not Critical): An identifier of the certificate owner’s public key in case more than one public key is available. It is recommended to use the hash value of the public key as an identifier.
- Certificate Subject Alternative Name (Not Critical): This extension can be used to associate alternative, non-X,500-based names to the certificate owner.
- Issuer Alternative Name (Not Critical): This extension can be used to associate alternative, non-X.500-based names to the certificate issuer.
- Certificate Key Usage (May be Critical or Not Critical): The Key Usage extension defines the purpose of the key contained in the certificate. Examples for possible purposes of TLS server certificates are digitalSignature, keyEncipherment, or keyAgreement.
- Extended Key Usage: (May be Critical or Not Critical): If this extension is marked as Critical, the indicated purposes, for example, Server Authentication replace the purposes given in the Certificate Key Usage Extension. Otherwise, the purposes given in this extension extend and explain the purposes in the Certificate Key Usage Extension.
- CRL Distribution Points (Not Critical): This extension defines how Certificate Revocation Lists (CRLs) can be obtained.
- Authority Information Access (AIA) (Not Critical): Information on services offered by the issuer of the certificate, especially about Online Certificate Status Protocol (OCSP) servers.
- Certificate Policies: (May be Critical or Not Critical): The Certificate Policies extension describes one or more certificate policies. Each policy contains an OID and further optional qualifiers. Moreover, the extension may include a URI to the issuer’s Certificate Practice Statement (CPS). In contrast to a certificate policy, a CPS does not apply to a single certificate, but describes the technical and organizational measures a CA takes for secure operation. It is therefore well suited to assess the level of trust to put into a CA.
- Basic Constraints (Critical): This extension specifies whether the presented certificate is a CA certificate or a so-called End Entity Certificate, that is, a certificate belonging to a person or a system, which cannot be used to sign other certificates. If the certificate is a CA certificate, the maximum path length for certificate chains can be constrained by means of this extension.
Note that the above Critical/Not Critical classification might differ from the guidelines of the Certification Authority Browser Forum (CA/Browser Forum), a consortium of certification authorities, web browser vendors, and companies providing PKI-based applications. The CA/Browser Forum guidelines govern the issuing and management of X.509v3 certificates, including those used for TLS [43].
Figure 10.2 shows some of the extension fields for the certificate of the www.amazon.com web server.
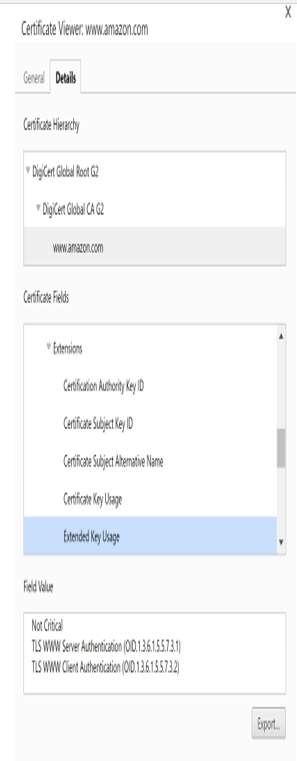
Figure 10.2: X.509v3 certificate extensions of www.amazon.com as shown by Google Chrome’s certificate viewer
Looking at these extensions, you can find a few terms and concepts we have not yet discussed. Let’s start with the question of how Alice can actually obtain an X.509 certificate from a CA.